Open source platforms can be used by criminals to instigate or conduct illegal activity and by terrorists to recruit and encourage new members, disseminate violent extremist messaging through video or documents, coordinate activities, and claim responsibility for attacks around the world. As such, law enforcement and analytic personnel should understand the uses of social media and be aware of social media tools that can be used to document criminal and terrorist activity. A wide variety of open source analysis tools—both no-cost and paid—is available to public and private sector organizations, including law enforcement and analytic personnel, and the technology continues to evolve. ROSA tools that access only publicly available information and are capable of searching multiple platforms simultaneously are assets for maximizing efficiency during authorized uses by law enforcement and analytic personnel.
Law enforcement agencies and fusion centers should regularly assess the tools available; understand, to the extent possible, how the tools work before employing them; confirm that the use of such tools is consistent with applicable law, regulation, and policy; require human review of any search results returned by an automated or semiautomated tool; and evaluate the impact of the new capabilities and/or tools on P/CRCL. Law enforcement agencies may reach out to state or major urban area fusion centers in their area of responsibility for additional information on ROSA tools and capabilities.
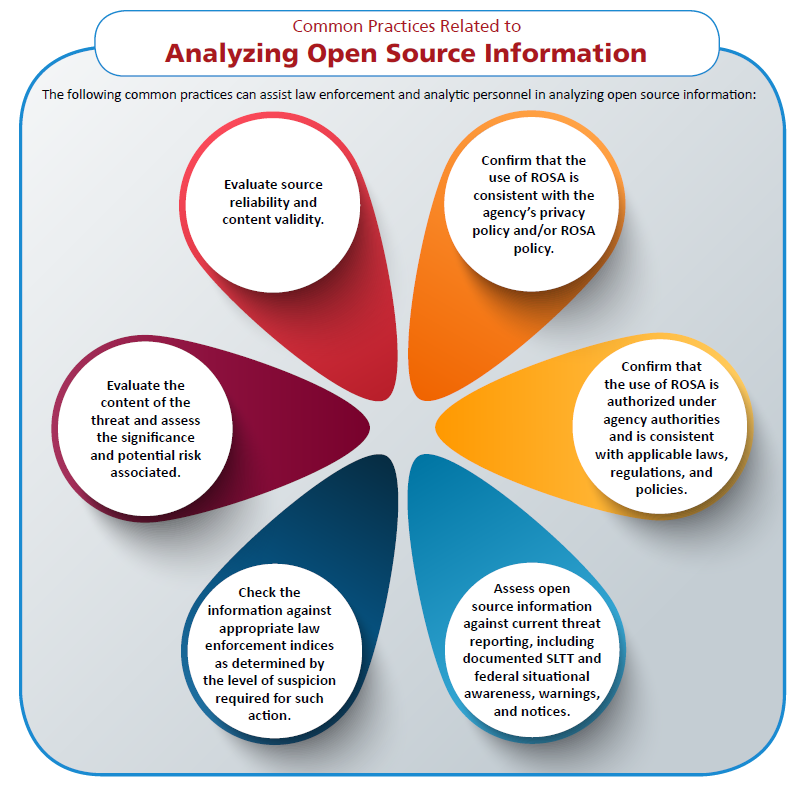
…
Recommended Practices for Law Enforcement and Analytic Personnel Using ROSA
- Have a strong policy in place on conducting ROSA before using open source analysis for investigative or law enforcement intelligence purposes. All policies and procedures must be compliant with the U.S. Constitution, the respective state’s constitution, and the applicable laws, rules, and regulations, as appropriate. Involve the privacy officer and legal counsel with the development and review of agency policies related to ROSA.
- Identify policy, training, and supporting resources that can help address context challenges when social media content is written in a foreign language or makes unfamiliar cultural references.
- Report violations or suspected violations of the agency policy.
- Focus only on public safety, criminal activity, and suspicious behavior, rather than on constitutionally protected expression or activities.
- Limit the collection of publicly available social media information to that which is reasonably related to the purpose of the search.
- Limit the collection to relevant contacts, connections, and the speech of others.
- Protected activity may take many forms, and social media platforms shape the message and its meaning. Protected speech can include text, emojis, pictures, videos, music and lyrics, and“Likes,” as well as the individual’s decision to post, share, respond, or repost.
- Specify that social media should only be collected without regard to an individual’s viewpoint or the fact of speaking itself, unless expressly relevant to the enforcement of a statute or regulation.
- Receive supervisory approval and oversight before conducting open source analysis.
- Establish an audit capability for ROSA activities (e.g., prior to conducting ROSA, law enforcement and analytic personnel may provide a supervisor sufficient information to support a ROSA request, and such requests could then be audited on a periodic basis).
- Retain social media postings in accordance with agency ROSA retention policy.
- Use only authorized accounts, as appropriate for the matter, to log in to social media sites. Adhere to the agency policy relating to online undercover activity, seeking supervisory approval, documenting the law enforcement or analytic personnel activity, periodically reviewing the activity, and auditing undercover processes and behaviors (including authorization time frames for undercover activities).
- Actively engage on social media sites only as permitted by agency policy.